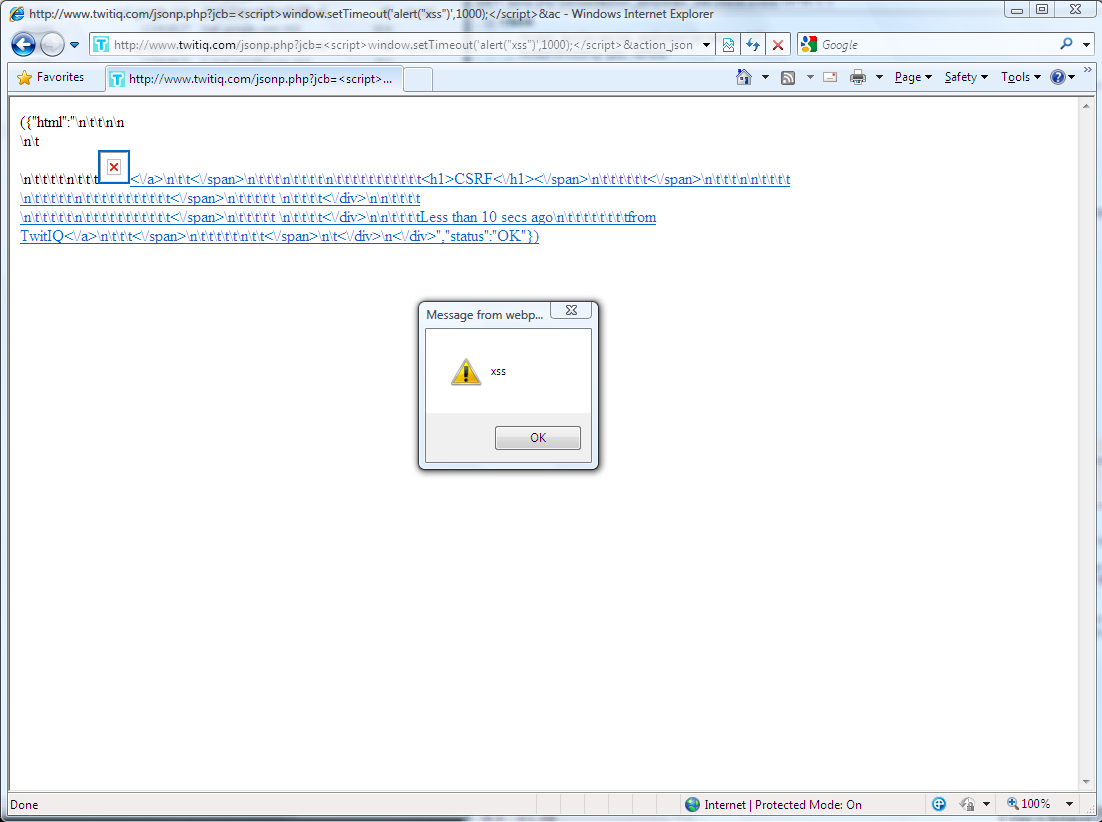
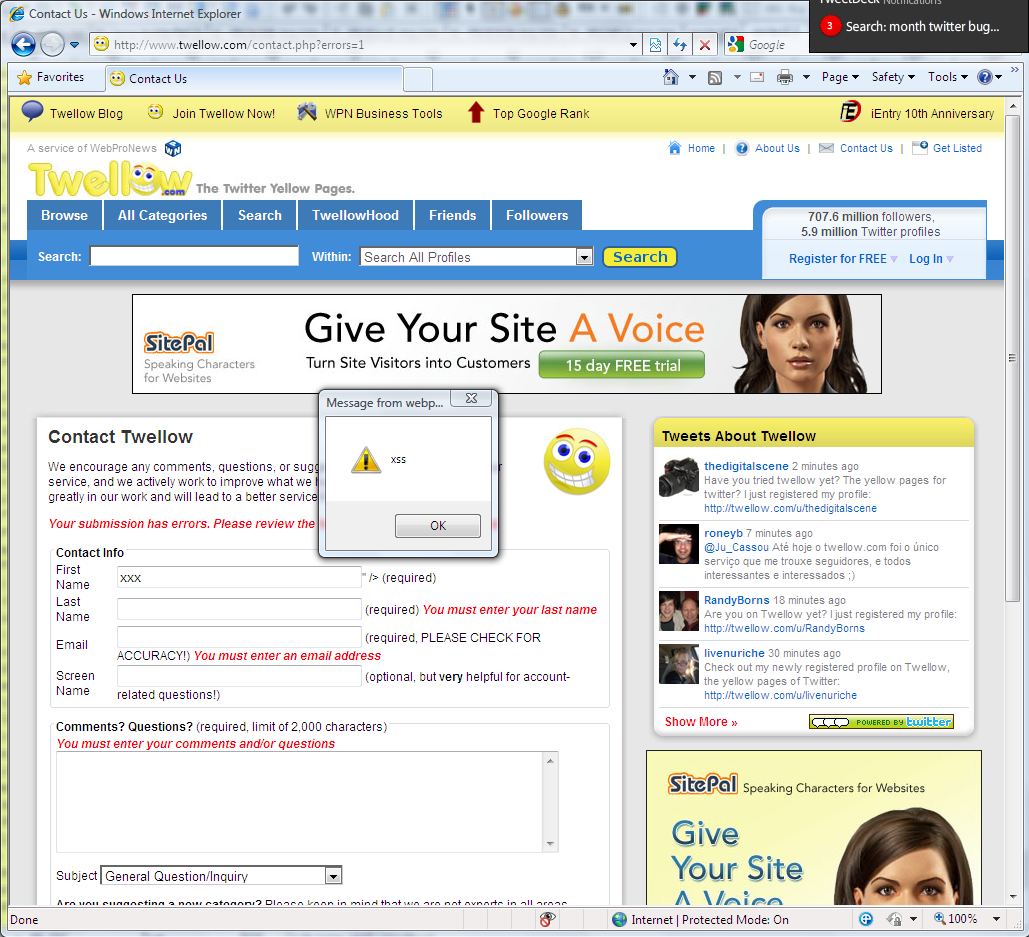
I’ve decided to gather and publish some statistics for the first 15 days of “Month of Twitter Bugs”.
There were 35 vulnerabilities disclosed for 15 different Twitter 3rd-party services.
12 of the 35 vulnerabilities were 0days (11 of them disclosed in the blog comments), which means there was no patch available at the time they were disclosed.
7 of those 0day vulnerabilities are still unpatched!
The average fix time for a vendor (not including bit.ly) is 18 hours.
The following pie chart shows the types of vulnerabilities found in MoTB.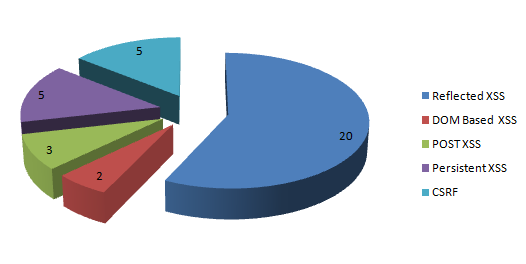
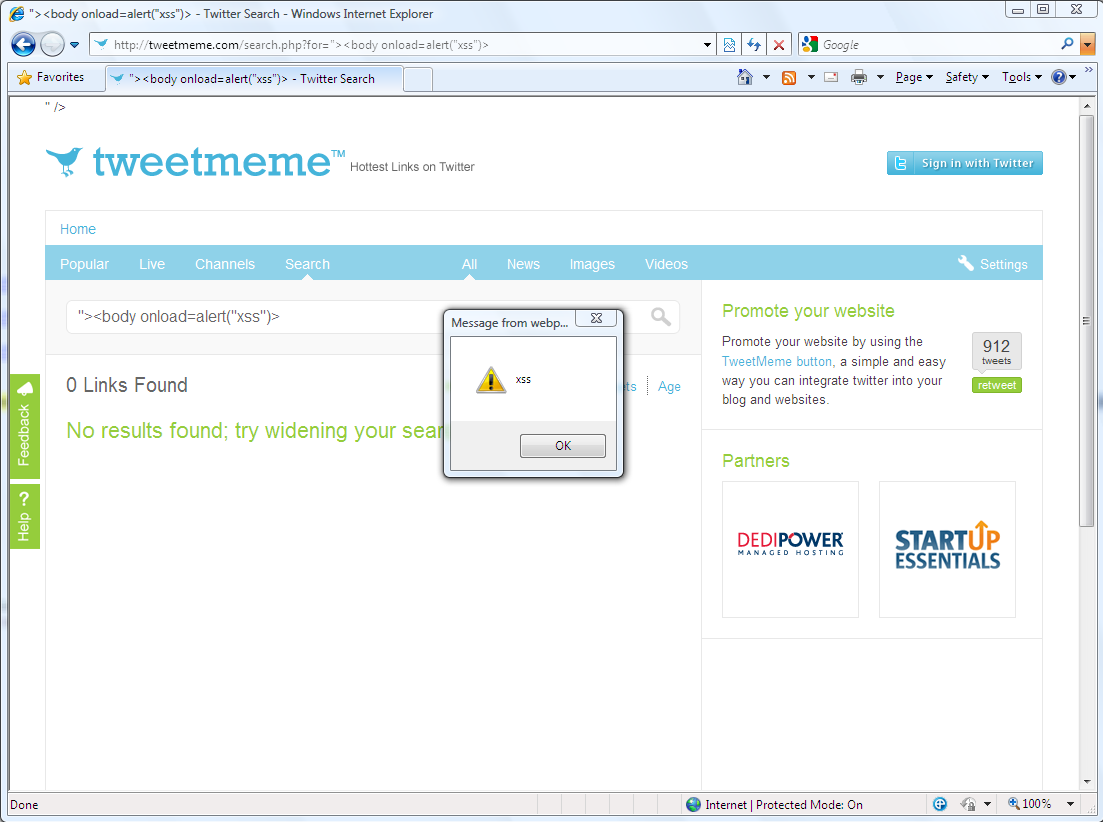
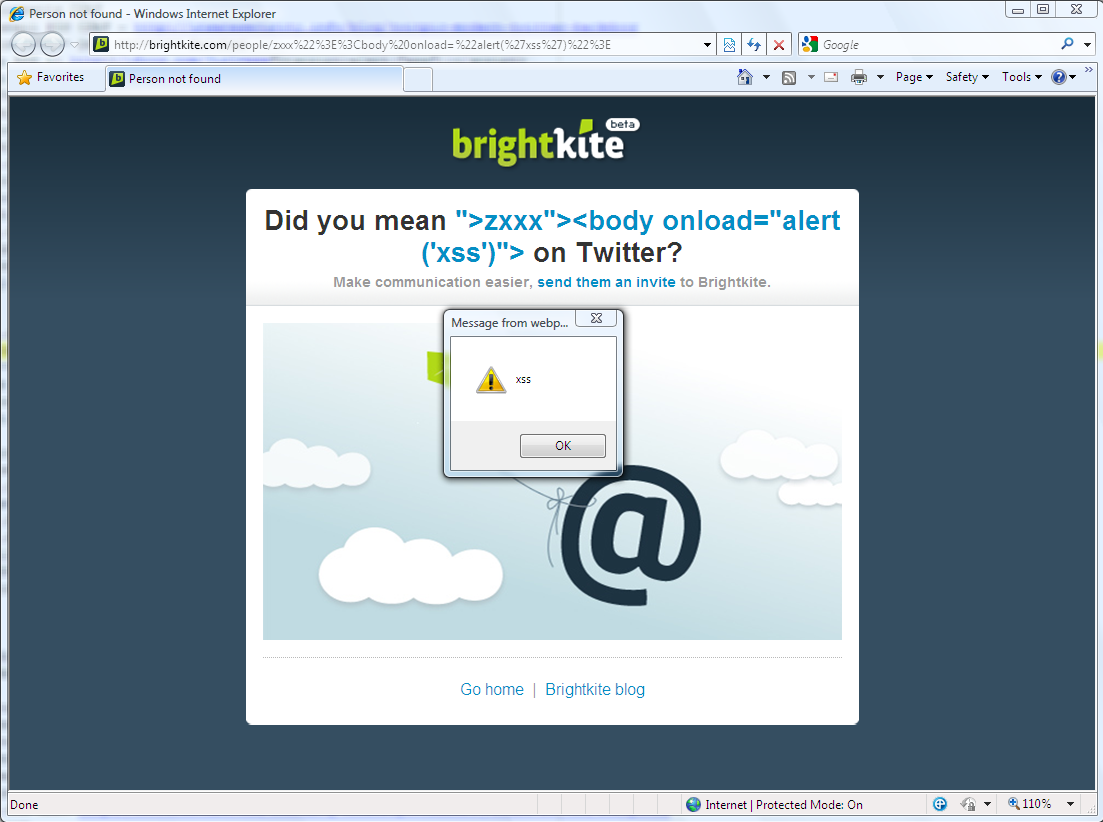
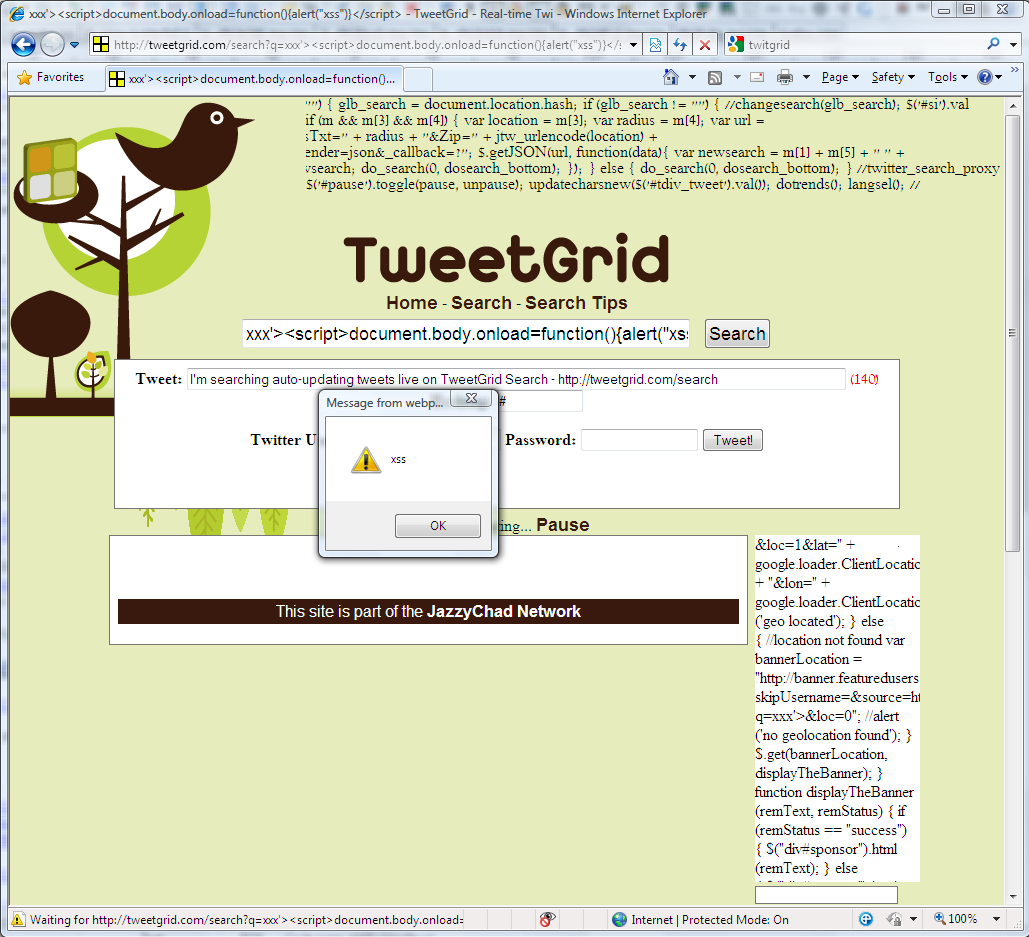
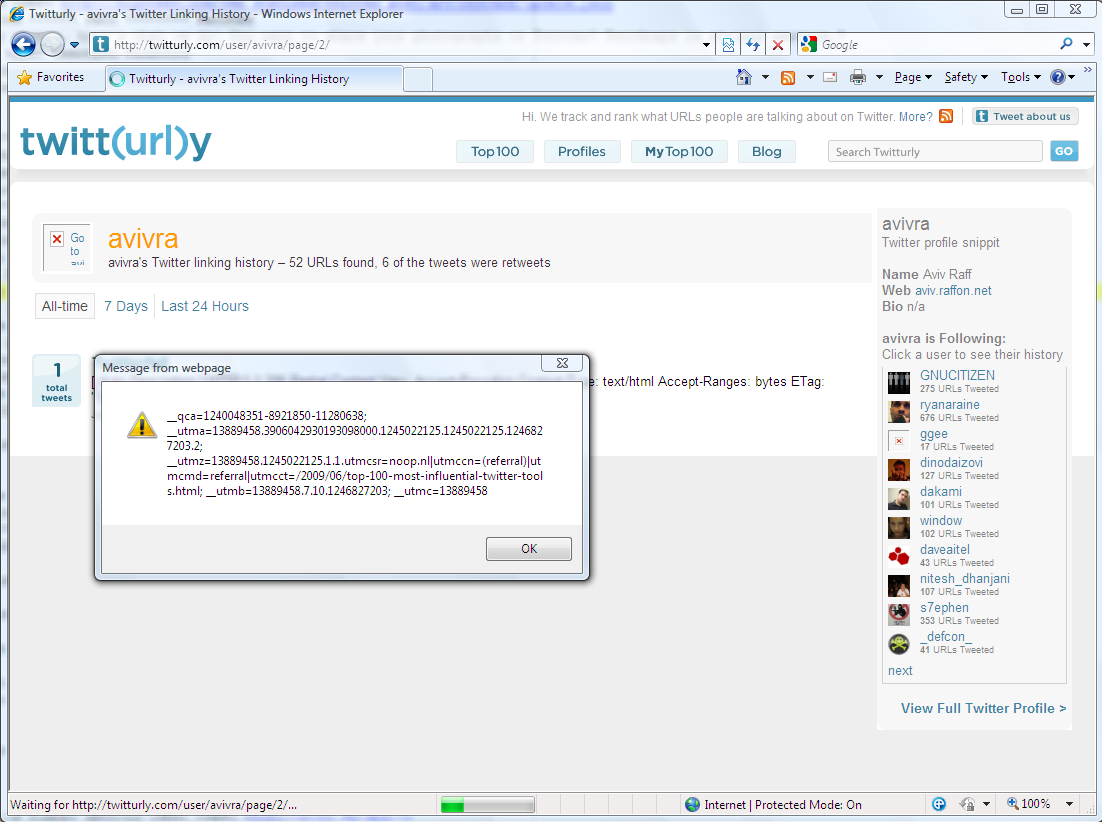
As a bonus for the “Halftime statistics report”, I would like to present a bug that was submitted by Laurent Gaffie: Twitter Search Web Server Information Leakage.
The Twitter search server did not block access to the “.htaccess” file, which revealed the configuration of the Twitter search web server, including a block list of IPs (spammers?).
Status: Fixed.
Screenshot: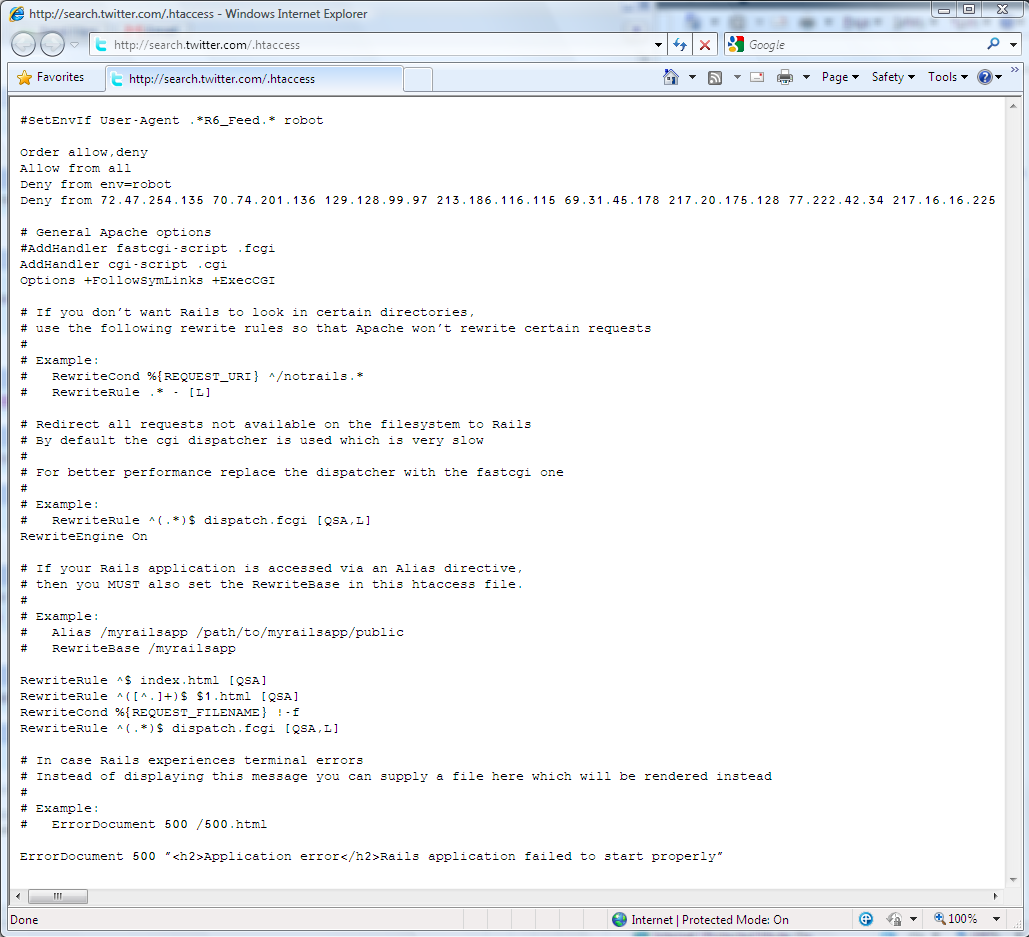
While this bug is nothing compared to the recent Twitter servers/employees hack disclosure, it still shows that Twitter needs to hire a security engineer, and fast!